Get to Know Trojans
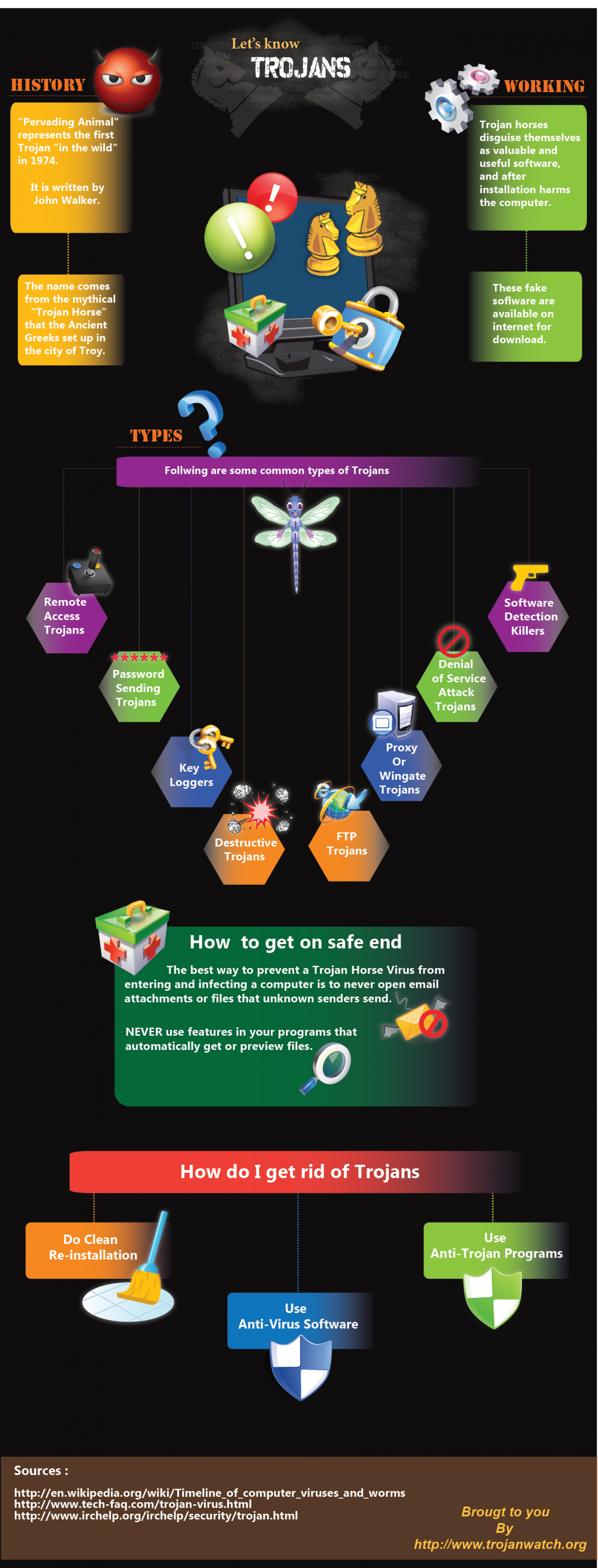
COUTE Let's know MRUTER VIRUS SCOMPU TROJANS DER VARUS HISTORY WORKING "Pervading Animal" represents the first Trojan "in the wild" in 1974. Trojan horses disguise themselves as valuable and useful software, COMPUTER VRUS and after It is written by installation harms John Walker. RUS the computer. TER YRUS ER VIRUS TRUS The name comes These fake from the mythical "Trojan Horse" that the Ancient soflware are CO available on internet for COMFU Greeks set up in the city of Troy. download. COM TYPES Follwing are some common types of Trojans Remote Software Access Detection Trojans Killers Denial Password Sending Trojans of Service Attack Trojans Proxy Or Wingate Trojans Key Loggers FTP Destructive Trojans Trojans How to get on safe end The best way to prevent a Trojan Horse Virus from entering and infecting a computer is to never open email attachments or files that unknown senders send. NEVER use features in your programs that automatically get or preview files. 0. How do I get rid of Trojans Do Clean Use Re-installation Anti-Trojan Programs Use Anti-Virus Software Sources : http://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms http://www.tech-faq.com/trojan-virus.html http://www.irchelp.org/irchelp/security/trojan.html Brougt to you By http://www.trojanwatch.org COUTE Let's know MRUTER VIRUS SCOMPU TROJANS DER VARUS HISTORY WORKING "Pervading Animal" represents the first Trojan "in the wild" in 1974. Trojan horses disguise themselves as valuable and useful software, COMPUTER VRUS and after It is written by installation harms John Walker. RUS the computer. TER YRUS ER VIRUS TRUS The name comes These fake from the mythical "Trojan Horse" that the Ancient soflware are CO available on internet for COMFU Greeks set up in the city of Troy. download. COM TYPES Follwing are some common types of Trojans Remote Software Access Detection Trojans Killers Denial Password Sending Trojans of Service Attack Trojans Proxy Or Wingate Trojans Key Loggers FTP Destructive Trojans Trojans How to get on safe end The best way to prevent a Trojan Horse Virus from entering and infecting a computer is to never open email attachments or files that unknown senders send. NEVER use features in your programs that automatically get or preview files. 0. How do I get rid of Trojans Do Clean Use Re-installation Anti-Trojan Programs Use Anti-Virus Software Sources : http://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms http://www.tech-faq.com/trojan-virus.html http://www.irchelp.org/irchelp/security/trojan.html Brougt to you By http://www.trojanwatch.org COUTE Let's know MRUTER VIRUS SCOMPU TROJANS DER VARUS HISTORY WORKING "Pervading Animal" represents the first Trojan "in the wild" in 1974. Trojan horses disguise themselves as valuable and useful software, COMPUTER VRUS and after It is written by installation harms John Walker. RUS the computer. TER YRUS ER VIRUS TRUS The name comes These fake from the mythical "Trojan Horse" that the Ancient soflware are CO available on internet for COMFU Greeks set up in the city of Troy. download. COM TYPES Follwing are some common types of Trojans Remote Software Access Detection Trojans Killers Denial Password Sending Trojans of Service Attack Trojans Proxy Or Wingate Trojans Key Loggers FTP Destructive Trojans Trojans How to get on safe end The best way to prevent a Trojan Horse Virus from entering and infecting a computer is to never open email attachments or files that unknown senders send. NEVER use features in your programs that automatically get or preview files. 0. How do I get rid of Trojans Do Clean Use Re-installation Anti-Trojan Programs Use Anti-Virus Software Sources : http://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms http://www.tech-faq.com/trojan-virus.html http://www.irchelp.org/irchelp/security/trojan.html Brougt to you By http://www.trojanwatch.org COUTE Let's know MRUTER VIRUS SCOMPU TROJANS DER VARUS HISTORY WORKING "Pervading Animal" represents the first Trojan "in the wild" in 1974. Trojan horses disguise themselves as valuable and useful software, COMPUTER VRUS and after It is written by installation harms John Walker. RUS the computer. TER YRUS ER VIRUS TRUS The name comes These fake from the mythical "Trojan Horse" that the Ancient soflware are CO available on internet for COMFU Greeks set up in the city of Troy. download. COM TYPES Follwing are some common types of Trojans Remote Software Access Detection Trojans Killers Denial Password Sending Trojans of Service Attack Trojans Proxy Or Wingate Trojans Key Loggers FTP Destructive Trojans Trojans How to get on safe end The best way to prevent a Trojan Horse Virus from entering and infecting a computer is to never open email attachments or files that unknown senders send. NEVER use features in your programs that automatically get or preview files. 0. How do I get rid of Trojans Do Clean Use Re-installation Anti-Trojan Programs Use Anti-Virus Software Sources : http://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms http://www.tech-faq.com/trojan-virus.html http://www.irchelp.org/irchelp/security/trojan.html Brougt to you By http://www.trojanwatch.org COUTE Let's know MRUTER VIRUS SCOMPU TROJANS DER VARUS HISTORY WORKING "Pervading Animal" represents the first Trojan "in the wild" in 1974. Trojan horses disguise themselves as valuable and useful software, COMPUTER VRUS and after It is written by installation harms John Walker. RUS the computer. TER YRUS ER VIRUS TRUS The name comes These fake from the mythical "Trojan Horse" that the Ancient soflware are CO available on internet for COMFU Greeks set up in the city of Troy. download. COM TYPES Follwing are some common types of Trojans Remote Software Access Detection Trojans Killers Denial Password Sending Trojans of Service Attack Trojans Proxy Or Wingate Trojans Key Loggers FTP Destructive Trojans Trojans How to get on safe end The best way to prevent a Trojan Horse Virus from entering and infecting a computer is to never open email attachments or files that unknown senders send. NEVER use features in your programs that automatically get or preview files. 0. How do I get rid of Trojans Do Clean Use Re-installation Anti-Trojan Programs Use Anti-Virus Software Sources : http://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms http://www.tech-faq.com/trojan-virus.html http://www.irchelp.org/irchelp/security/trojan.html Brougt to you By http://www.trojanwatch.org COUTE Let's know MRUTER VIRUS SCOMPU TROJANS DER VARUS HISTORY WORKING "Pervading Animal" represents the first Trojan "in the wild" in 1974. Trojan horses disguise themselves as valuable and useful software, COMPUTER VRUS and after It is written by installation harms John Walker. RUS the computer. TER YRUS ER VIRUS TRUS The name comes These fake from the mythical "Trojan Horse" that the Ancient soflware are CO available on internet for COMFU Greeks set up in the city of Troy. download. COM TYPES Follwing are some common types of Trojans Remote Software Access Detection Trojans Killers Denial Password Sending Trojans of Service Attack Trojans Proxy Or Wingate Trojans Key Loggers FTP Destructive Trojans Trojans How to get on safe end The best way to prevent a Trojan Horse Virus from entering and infecting a computer is to never open email attachments or files that unknown senders send. NEVER use features in your programs that automatically get or preview files. 0. How do I get rid of Trojans Do Clean Use Re-installation Anti-Trojan Programs Use Anti-Virus Software Sources : http://en.wikipedia.org/wiki/Timeline_of_computer_viruses_and_worms http://www.tech-faq.com/trojan-virus.html http://www.irchelp.org/irchelp/security/trojan.html Brougt to you By http://www.trojanwatch.org
Get to Know Trojans
Source
http://www.t...w-trojans/Category
ComputersGet a Quote