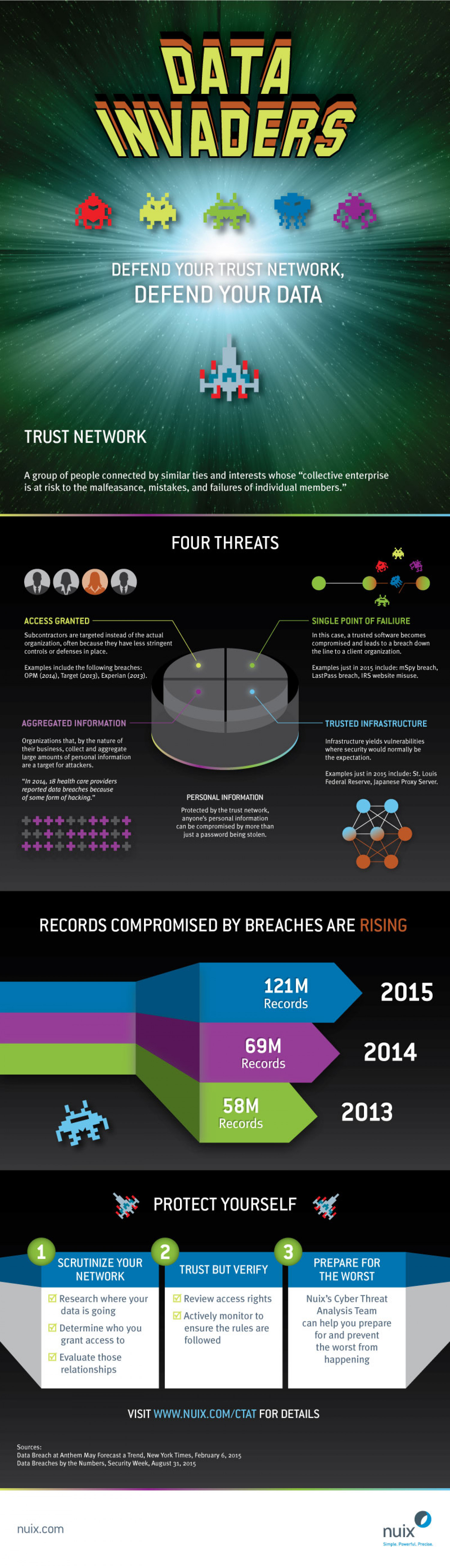
Data Invaders: Defend Your Trust Network, Defend Your Data
DATA INVADERS DEFEND YOUR TRUST NETWORK, DEFEND YOUR DATA TRUST NETWORK A group of people connected by similar ties and interests whose "collective enterprise is at risk to the malfeasance, mistakes, and failures of individual members." FOUR THREATS 0000 ACCESS GRANTED SINGLE POINT OF FAILIURE Subcontractors are targeted instead of the actual organization, often because they have less stringent controls or defenses in place. In this case, a trusted software becomes compromised and leads to a breach down the line to a client organization. Examples include the following breaches: OPM (2014), Target (2013), Experian (2013). Examples just in 2015 include: mSpy breach, LastPass breach, IRS website misuse. GREGATED TRUSTED INFRASTRUCTURE Organizations that, by the nature of their business, collect and aggregate large amounts of personal information are a target for attackers. Infrastructure yields vulnerabilities where security would normally be the expectation. Examples just in 2015 include: St. Louis Federal Reserve, Japanese Proxy Server. "In 2014, 18 health care providers reported data breaches because of some form of hacking." PERSONAL INFORMATION Protected by the trust network, anyone's personal information can be compromised by more than just a password being stolen. RECORDS COMPROMISED BY BREACHES ARE RISING 121M 2015 Records 69M 2014 Records 58M 2013 Records PROTECT YOURSELF 3. PREPARE FOR SCRUTINIZE YOUR TRUST BUT VERIFY NETWORK THE WORST Z Research where your data is going Z Review access rights Nuix's Cyber Threat Analysis Team can help you prepare for and prevent M Actively monitor to 7 Determine who you ensure the rules are grant access to followed the worst from Z Evaluate those relationships happening VISIT WWW.NUIX.COM/CTAT FOR DETAILS Sources: Data Breach at Anthem May Forecast a Trend, New York Times, February 6, 2015 Data Breaches by the Numbers, Security Week, August 31, 2015 nuix.com nuix Simple. Powertul Precise.
Data Invaders: Defend Your Trust Network, Defend Your Data
Source
http://www.n...nfographicCategory
ComputersGet a Quote