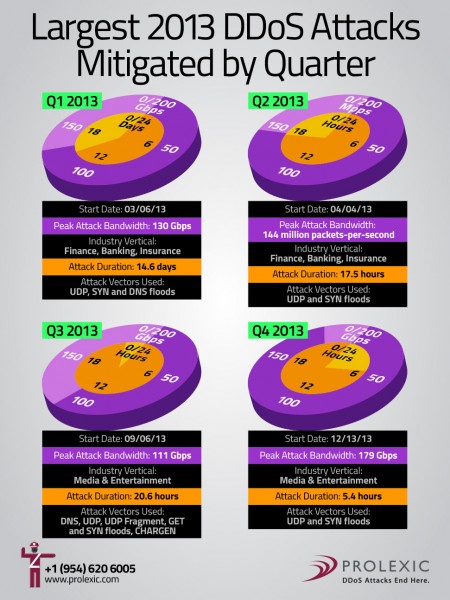
DDoS Attacks & DDoS Defense
DDOS Attacks & Defense MOTIVATION Hacktivism - Extortion ▪ Retaliation By Competitors Angry Employees or Customers - Hacker Experiments IDENTIFY TARGET Web Servers - DNS Servers . Email Servers FTP Servers - Network Devices INVESTIGATE TARGET Footprint Network - Port Scan LAUNCH DDOS ATTACK Use tool to specify: • Target · Port - Attack Types (Layer 3, 4 & 7) Attack Vectors (DNS, UDP, SYN, etc.) Duration Dirt jumper v3 Tima: 23:42.34 Onine No Protection, Appliance, CDN, Telco, ISP Prolexic DD0S Protection Monitoring/alerting • 15-minute mitigation SLA 1.5 Tbps cloud platform 50 Gbps Malicious Traffic 24/7 SOC 50 Gbps · Attack too big · Attack too complex Clean Traffic ERROR 404 File not found Welcone to WoriBanitor.com The page might have been m Pugje Clean Traffic is temporaniy unuvalte PROLEXIC DDOS Attacks End Here. www.prolexic.com DDOS ATTACKS DDOS DEFENSE
DDoS Attacks & DDoS Defense
Source
http://www.p...aphic.htmlCategory
TechnologyGet a Quote