Lifecycle of a Deleted File
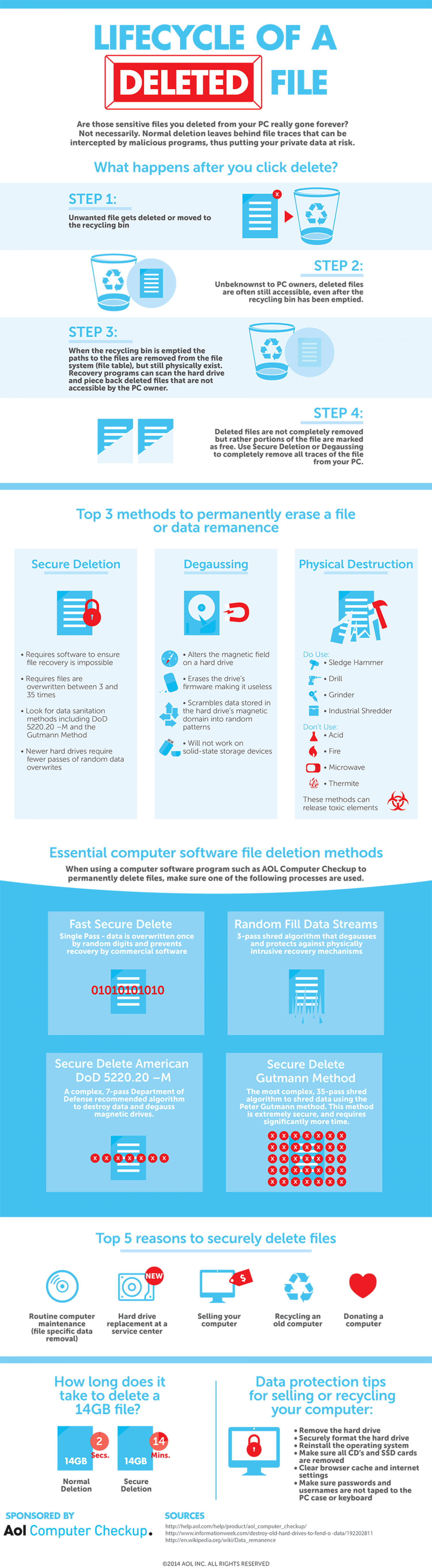
LIFECYCLE OF A DELETED FILE Are those sensitive files you deleted from your PC really gone forever? Not necessarily. Normal deletion leaves behind file traces that can be intercepted by malicious programs, thus putting your private data at risk. What happens after you click delete? STEP 1: Unwanted file gets deleted or moved to the recycling bin STEP 2: Unbeknownst to PC owners, deleted files are often still accessible, even after the recycling bin has been emptied. STEP 3: When the recycling bin is emptied the paths to the files are removed from the file system (file table), but still physically exist. Recovery programs can scan the hard drive and piece back deleted files that are not accessible by the PC owner. STEP 4: FF Deleted files are not completely removed but rather portions of the file are marked as free. Use Šecure Deletion or Degaussing to completely remove all traces of the file from your PC. Top 3 methods to permanently erase a file or data remanence Secure Deletion Degaussing Physical Destruction • Requires software to ensure file recovery is impossible • Alters the magnetic field on a hard drive Do Use: >• Sledge Hammer • Requires files are overwritten between 3 and 35 times • Erases the drive's firmware making it useless • Drill • Grinder • Look for data sanitation methods including DoD 5220.20 -M and the Gutmann Method • Scrambles data stored in the hard drive's magnetic domain into random patterns • Industrial Shredder Don't Use: • Acid • Will not work on solid-state storage devices • Newer hard drives require fewer passes of random data overwrites • Fire • Microwave • Thermite These methods can release toxic elements Essential computer software file deletion methods When using a computer software program such as AOL Computer Checkup to permanently delete files, make sure one of the following processes are used. Fast Secure Delete Random Fill Data Streams Single Pass - data is overwritten once by random digits and prevents recovery by commercial software 3-pass shred algorithm that degausses and protects against physically intrusive recovery mechanisms 01010101010 Secure Delete American Secure Delete DoD 5220.20 -M Gutmann Method A complex, 7-pass Department of Defense recommended algorithm to destroy data and degauss magnetic drives. The most complex, 35-pass shred algorithm to shred data using the Peter Gutmann method. This method is extremely secure, and requires significantly more time. Top 5 reasons to securely delete files NEW Routine computer maintenance (file specific data removal) Selling your computer Hard drive Recycling an old computer Donating a computer replacement at a service center How long does it take to delete a 14GB file? Data protection tips for selling or recycling your computer: • Remove the hard drive • Securely format the hard drive • Reinstall the operating system • Make sure all CD's and sSD cards are removed Clear settings • Make sure passwords and usernames are not taped to the PC case or keyboard 14 Secs. 14GB Mins. 14GB browser cache and internet Normal Deletion Secure Deletion SPONSORED BY SOURCES http://help.aol.com/help/product/aol_computer_checkup/ Aol Computer Checkup. http://www.informationweek.com/destroy-old-hard-drives-to-fend-o -data/192202811 http://en.wikipedia.org/wiki/Data_remanence ©2014 AOL INC. ALL RIGHTS RESERVED Ш ШШ
Lifecycle of a Deleted File
Source
http://compu...eted-file/Category
ComputersGet a Quote