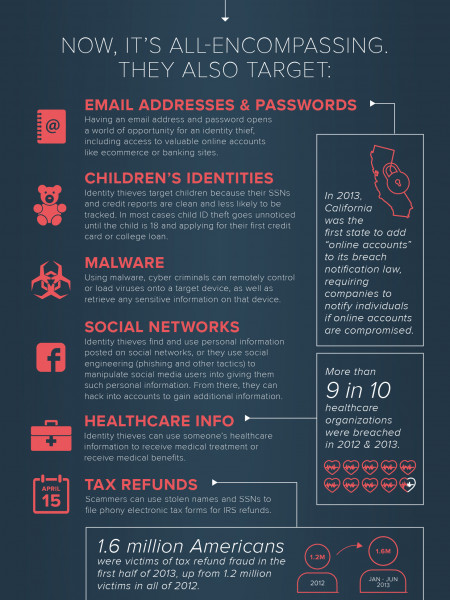
How Hackers Steal Your Data
AT ITS MOST BASIC, A DATA BREACH CONSISTS OF THREE ELEMENTS: AS ANYONE WHO WATCHES HEIST OR SPY MOVIES WILL KNOW, BREAKING IN MAY BE HARD, BUT IT IS ONLY THE START OF THE STORY. NEXT YOU HAVE TO LOCATE AND OBTAIN YOUR TARGET, AND FINALLY - AND MOST CRITICALLY - YOU HAVE TO GET IT OUT SAFELY. 000 INFILTRATION AGGREGATION EXFILTRATION METHOD OF ENTRY WHAT HACKERS ARE TARGETING GETTING THE DATA OUT A 55% 2% 85% 2% 48% 2% INSIDER: LEGITIMATE ACCESS AUTHENTICATION ATTACKER'S EMAIL EXISTING REMOTE PAYMENT MALWARE ACCESS APPLICATION CARD DATA CREDENTIALS 8% 2% 8% 2% O 44% 2% SOCIAL PHYSICAL SENSITIVE CUSTOMER EXISTING PHYSICAL ENGINEERING ACCESS COMPANY DATA RECORDS PROTOCOLS ACCESS 6% 2% 3% 4% CARD DATA IS READILY HSQL DATA MAY BE HARVESTED SALEABLE ON THE BLACK PERIODICALLY TO A FILE EMAIL MARKET, SO IS THE PRIME REMOTE FILE TRADE SQL AND THEN UPLOADED VIA TROJAN INCLUSION SECRETS TARGET FOR THIEVES. INJECTION THE NETWORK, OR IN SOME CASES IT MAY EVEN BE RETRIEVED IN REAL TIME. Source: Trustwave Global Security Report 201l Source: Trustwave Global Security Report 2011l 6% 20% SQL UNKNOWN / OTHER INJECTION Source: Trustwave Global Security Report 201l 45,000 O APRIL 8 - First reports of public exploitation ADOBE'S CVE-2011-0611 VULNERABILITY: WHEN THE ATTACKS CAME IN 40,000 O APRIL 11 - Adobe Advisory APSA11-02; MMPC receives its first public sample 35,000 THE MAJORITY OF ATTACKERS GET IN THROUGH AVAILABLE REMOTE ACCESS TOOLS, OFTEN BECAUSE THE LOGIN AND PASSWORD DATA HAVE NOT BEEN CHANGED FROM THE DEFAULT. HOWEVER, A SIGNIFICANT PROPORTION ALSO RELY ON TRICKING USERS ONE WAY OR ANOTHER INTO DOING 30,000 O APRIL 12 - MMPC signature released 25,000 O APRIL 15 - Flash Player update SOMETHING THEY SHOULDN'T. 20,000 O APRIL 21 - Adobe Reader / Acrobat updates 15,000 ZERO DAY 10,000 1 MONTH AFTER UPDATE O 2+ MONTHS AFTER UPDATES O 5,000 2 5 8 11 14 17 20 4 7 10 13 16 19 22 25 28 1 4 7 10 13 16 19 22 25 28 31 JUNE 8 11 14 17 20 23 26 29 23 26 29 Source: Microsoft APRIL MAY JULY HSQL
How Hackers Steal Your Data
Publisher
Raconteur MediaSource
http://www....K)/2412324Category
ComputersGet a Quote